A Practical Guide for High-Quality Cybersecurity RFP Responses
This guide explains how these RFPs are evaluated and how to produce accurate, compliant responses that stand up to legal and procurement reviews.

Cybersecurity is now one of the most scrutinized decisions in procurement. With global spending projected to reach $302 billion by 2029, RFPs are becoming longer, more technical, and more risk-driven.
Generic boilerplate language no longer works. If your response mentions "encryption" without specifying standards, or "incident response" without clear timelines, you lose credibility. Buyers are trained to find the gaps that could lead to post-breach liability.
To win, your responses must be precise and internally consistent. You need to prove technical maturity under tight deadlines without exhausting your security and compliance experts.
This guide explains how these RFPs are evaluated and how to produce accurate, compliant responses that stand up to legal and procurement reviews.
Key Takeaways
- Cybersecurity RFPs function as risk and accountability documents, where every response can influence contracts, audits, and post-incident scrutiny.
- Manual response processes break down under the weight of long questionnaires, cross-functional dependencies, and constant security and compliance changes.
- Response quality plays a direct role in win rates, as buyers favor clear, accurate, and internally consistent answers over generic or reused content.
- Inconsistencies across technical, compliance, and legal sections are one of the fastest ways to lose credibility and trigger extended review cycles.
- AI-powered RFP workflows and Inventive AI are becoming a competitive necessity for teams that need to respond faster, reduce risk, and scale high-quality cybersecurity proposals without adding headcount.
What Is a Cybersecurity RFP?
A cybersecurity RFP is a formal procurement document used to evaluate vendors that will handle, protect, or have access to sensitive systems and data. It defines technical security requirements, compliance expectations, incident response obligations, and required evidence such as policies, audits, and certifications.
Responses are treated as formal representations and are frequently incorporated into contracts, SOWs, and security assessments.
Why Cybersecurity RFPs Are More Complex Than Standard RFPs?
Cybersecurity RFPs go deeper than feature lists or pricing tables. They test how a vendor operates, governs risk, and proves security posture across technical, legal, and organizational layers.
- Security requirements span multiple frameworks, including CIS Controls, ISO 27001, and industry regulations.
- Questions overlap across sections like access control, logging, monitoring, and incident response.
- Responses must align across RFP sections, security questionnaires, and legal language.
- Multiple internal stakeholders contribute answers under tight deadlines.
- Buyers expect evidence, not descriptions, including audits, policies, and operational details.
Together, these factors turn cybersecurity RFPs into high-effort, high-risk responses where consistency, proof, and coordination directly affect buyer confidence and evaluation outcomes.
7 Cybersecurity RFP Types and the Risks Buyers Are Evaluating
Cybersecurity RFPs are not issued from a single template. Buyers structure them around the specific risk they aim to control, the environment being protected, and the level of vendor access.
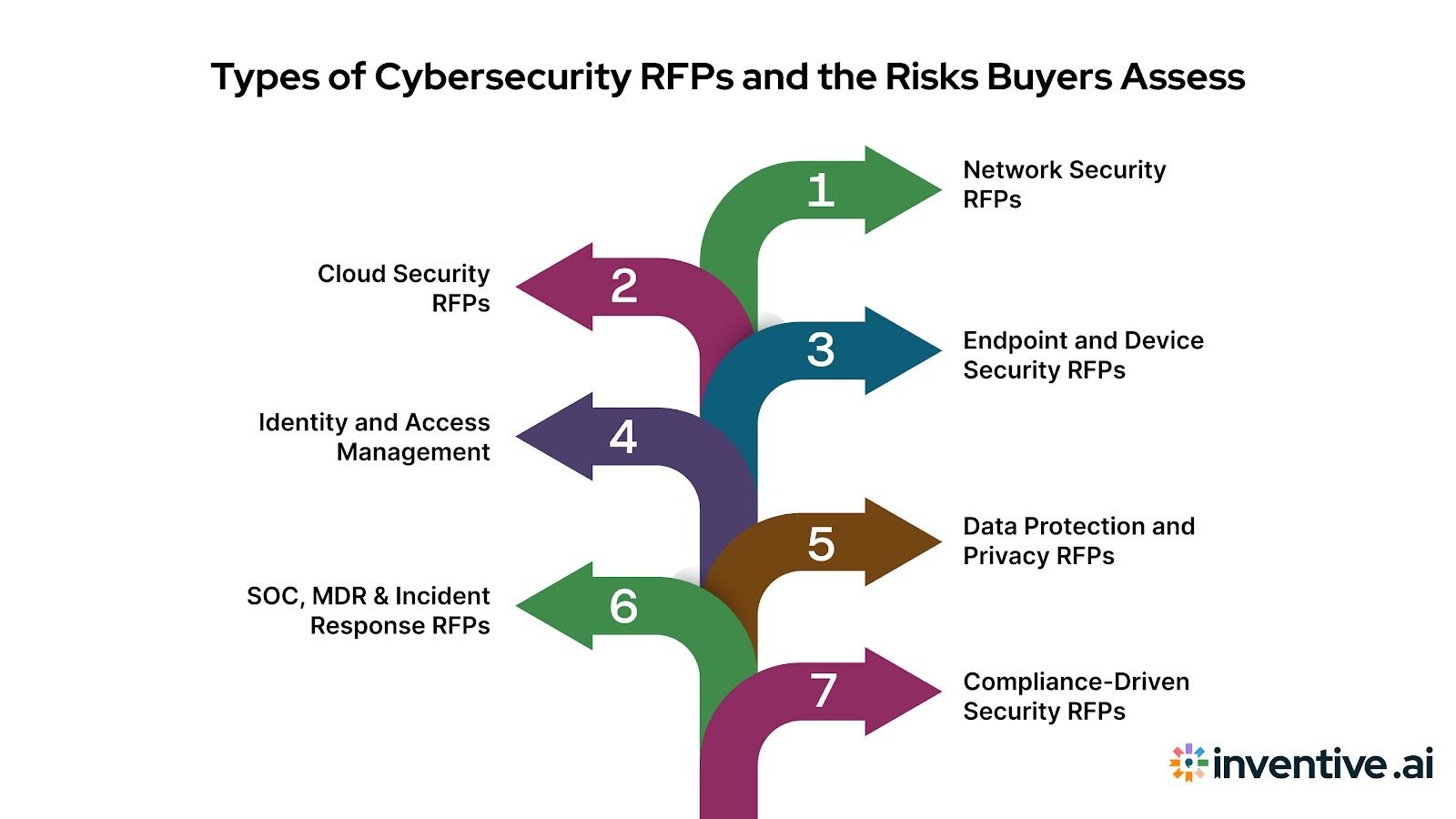
Below are the most common types of cybersecurity RFPs buyers issue, based on the security capability or risk area being evaluated.
- Network Security RFPs: Focus on perimeter and internal network controls, including firewalls, intrusion detection and prevention, segmentation, traffic inspection, and network monitoring.
- Cloud Security RFPs: Center on securing cloud infrastructure and workloads, including configuration management, visibility across environments, shared responsibility models, and integration with cloud-native services.
- Endpoint and Device Security RFPs: Evaluate how laptops, servers, mobile devices, and workloads are protected through EDR, device control, monitoring, and response capabilities.
- Identity and Access Management (IAM) RFPs: Address authentication, authorization, privileged access, identity lifecycle management, and enforcement of least-privilege access across systems.
- Data Protection and Privacy RFPs: Focus on how sensitive data is classified, encrypted, monitored, retained, and protected across systems, including alignment with privacy regulations.
- SOC, MDR, and Incident Response RFPs: Evaluate detection, monitoring, investigation, and response capabilities, including SLAs, escalation paths, and operational readiness.
- Compliance-Driven Security RFPs: Issued to meet regulatory or framework requirements such as HIPAA, SOC 2, ISO 27001, or industry-specific mandates, with heavy emphasis on evidence and audit alignment.
Some RFPs focus narrowly on a single control domain, while others bundle multiple security functions into a single evaluation to reduce vendor sprawl and simplify oversight.
Your response strategy should account for that difference. Narrowly scoped RFPs give you room to demonstrate depth and clarity in a specific control area, while bundled RFPs give you an opportunity to show consistency across architecture, compliance, and operational responses.
What Buyers Typically Include in Cybersecurity RFPs? 7 Pointers You Need to Know!
Cybersecurity RFPs follow a familiar structure, even when the scope varies. Buyers use these sections to force vendors to explain how their security controls operate in practice, how decisions are made under pressure, and how accountability is defined once a contract is signed.
Below are the sections and question patterns you will commonly encounter in a cybersecurity RFP.
1. Project Overview and Company Context
This section describes the buyer’s environment, business model, and risk exposure. It often looks harmless, but it sets the context for everything that follows. Buyers expect you to tailor your answers to their operating reality.
2. Scope of Work and Deliverables
Here, buyers define what they expect you to do, what you own operationally, and where responsibility stops. This includes functional requirements, implementation expectations, reporting obligations, and testing or QA requirements.
3. Technical and Security Requirements
This is the core of most cybersecurity RFPs. Buyers outline required controls across areas such as network security, identity, endpoint protection, logging, monitoring, and data protection. These requirements are often mapped to frameworks or regulations and repeated in different forms across the document.
4. Incident Response and Operational Questions
Nearly every cybersecurity RFP includes detailed questions about how incidents are detected, investigated, escalated, and resolved. You are typically asked about investigation phases, escalation paths, communication methods, response timelines, and the scope of remediation support.
5. Service Delivery, SLAs, and Metrics
This section focuses on how your service operates over time. Questions about implementation timelines, analyst retention rates, escalation staffing, and SLA metrics such as MTTD (Mean Time to Detect) and MTTR (Mean Time to Respond) are common. Buyers are assessing operational maturity and continuity, especially for managed or monitoring services.
6. Compliance, Legal, and Contractual Requirements
Buyers use this section to align security claims with legal accountability. It includes regulatory requirements, data protection obligations, confidentiality terms, audit rights, and liability language.
7. Evaluation Criteria and Submission Instructions
This section explains how responses will be scored and how proposals must be submitted. While it looks procedural, it tells you where buyers place weight. Some emphasize technical depth, others operational maturity, others cost or timeline.
Cybersecurity RFPs are structured to test the same claims repeatedly across different sections. Responses fail when the access control model described in Section 3 contradicts the identity workflow described in the security questionnaire. You have to keep your security story coherent as it moves from technical controls to operations to legal commitments.
Why Cybersecurity RFPs Are So Hard for Vendors to Respond To?
Cybersecurity RFPs are difficult to respond to because the services being evaluated are not discrete or static.
A single cybersecurity offering typically combines multiple products, service tiers, response commitments, asset coverage assumptions, and customer responsibilities. RFPs attempt to capture all of that through fixed questions that assume stable boundaries, which creates friction between how services are delivered and how they are described.
That friction appears in several consistent ways across cybersecurity RFPs.
- Extremely long and repetitive questionnaires: Cybersecurity RFPs repeat the same controls across technical sections, security questionnaires, and compliance forms. Each version uses different wording and expects a slightly different level of detail, which forces vendors to restate the same answer multiple times.
- Heavy reliance on SMEs across functions: Security teams answer control questions, legal reviews liability and contract language, and compliance maps frameworks. These inputs are produced separately and merged late in the process, which makes alignment slow and brittle.
- Constantly changing security requirements: Framework updates, new regulations, and buyer-specific standards mean questions change from one RFP to the next. Content that worked recently often needs rework to fit current expectations.
- Stale or conflicting security content: Responses are pulled from past RFPs, shared documents, and spreadsheets that reflect different versions of the service. When reused together, contradictions appear even when each answer was accurate on its own.
- Tight deadlines tied to high-value deals: Cybersecurity RFPs are often associated with renewals, replacements, or risk-driven timelines. The volume of review required rarely matches the time available to reconcile answers.
What makes cybersecurity RFPs difficult is the accumulation of these conditions. The document requires vendors to describe complex, evolving services multiple times, under different assumptions, and across different review lenses. Small inconsistencies become visible as the response moves from section to section, even when the underlying service has not changed.
Related: What is an RFP? Key Components of an Effective RFP
How to Respond to Cybersecurity RFPs With Confidence and Control?
Cybersecurity RFPs are not evaluated the same way as general technology proposals. The responses are reviewed by security, legal, compliance, and procurement teams, often in parallel. Each group reads the answers through a different lens, but they all rely on the same document.
Responding effectively means translating how security actually works inside the organization into language that holds up across technical, compliance, and legal review.
Below, we break down how teams approach that translation when responding to real cybersecurity RFPs under time pressure.
1. Anchor Every Answer in Risk Ownership
Cybersecurity questions in RFPs are rarely about whether you use a specific product. They are about how risk is identified, handled, and owned. Many responses fail because they read like a list of tools rather than an explanation of how security decisions are made and enforced. Reviewers look for evidence that controls operate within a broader risk management approach, not in isolation.
What to do in practice:
- Read each question and identify the risk it is probing, such as data exposure, incident delay, or third-party access.
- Frame responses around how that risk is managed, monitored, and reviewed.
- Mention tools only where they support the process being described.
Example: Instead of listing EDR, SIEM, and firewall tools, describe how suspicious activity is detected, escalated, investigated, and resolved, then reference the tools that support those steps.
2. Explain Security Controls Clearly Without Exposing Sensitive Internals
Cybersecurity RFP responses are reviewed by multiple reviewers with varying priorities. Security teams look for enough detail to understand how a control works. Legal teams look for language that could turn into a contractual obligation. Procurement looks for clarity and comparability across vendors.
When an answer is too short, reviewers cannot tell whether the control exists or is enforced. When an answer goes too deep into configurations or internal architecture, it raises follow-up questions about liability, scope, and exposure.
As a result, responses that describe processes, ownership, and outcomes tend to move through review faster than responses that are either vague or overly technical.
What to do in practice
- Describe processes, ownership, and outcomes rather than internal configurations.
- State when details are restricted and offer to discuss them separately.
- Keep the level of detail consistent across all security answers.
Example: For encryption questions, describe where encryption is applied, how keys are managed at a high level, and who controls access, without documenting exact key lengths or configurations.
3. Involve the Right Security Stakeholders Early
Cybersecurity answers are rarely owned by one person. Security, legal, compliance, and IT all contribute, often under tight deadlines. Responses break when assumptions are made or when inputs arrive too late to reconcile differences.
What to do in practice:
- Identify which questions require security, legal, or compliance input before drafting.
- Route those questions directly to the appropriate owners.
- Consolidate responses early enough to resolve conflicts.
Example: Have security confirm incident response workflows, legal review notification commitments, and compliance validate framework mappings before finalizing the answers.
4. Treat Compliance Answers as Enforceable Commitments
Compliance sections in cybersecurity RFPs are reviewed alongside contract language, not in isolation. Statements made in these sections are often referenced later during legal review, audits, or renewals.
When a response claims broad alignment without clearly defining scope, it creates ambiguity about what is actually covered by the service. Responses that describe controls as currently enforced and limit claims to the proposed services tend to progress through review with fewer follow-ups than responses that imply future or aspirational compliance.
What to do in practice
- Map compliance claims to current controls and policies.
- Limit statements to the scope of services being proposed.
- Avoid agreeing to requirements that cannot be met operationally.
Example: If asked about ISO 27001 alignment, clarify whether controls are certified, aligned, or partially implemented, and specify which services the alignment applies to.
5. Support Claims With Verifiable Evidence
Cybersecurity RFPs are reviewed by people who verify assertions. Claims without evidence slow reviews and trigger follow-up questions. Evidence carries more weight when it is tied directly to the answer it supports.
What to do in practice
- Identify claims that reviewers are likely to validate.
- Reference certifications, audits, or assessments at the point of the claim.
- Ensure evidence covers the same scope as the proposed service.
Example: When describing logging and monitoring, reference the SOC 2 report section that covers those controls instead of listing the certification generically.
6. Use Case Examples to Demonstrate Operational Reality
Abstract descriptions make it hard for reviewers to understand how controls work under pressure. Short, concrete examples help bridge that gap without turning the response into a case study.
What to do in practice
- Use brief scenarios to illustrate detection, escalation, or response.
- Keep examples aligned with the buyer’s environment or risk profile.
- Avoid marketing language or hypothetical success stories.
Example: Describe how a high-severity alert is triaged, escalated to an on-call analyst, and communicated to the customer within defined timelines.
7. Clarify Third-Party and Vendor Responsibilities Explicitly
Many cybersecurity RFPs probe how third-party risk is managed. Buyers often expect accountability to extend beyond direct systems.
What to do in practice
- Identify which third parties may access or process customer data.
- Describe how those vendors are vetted and monitored.
- State who owns remediation if a third party is involved in an incident.
Example: If using a cloud provider or managed service, explain how security responsibilities are divided and how incidents involving that provider are handled.
How AI Is Transforming Cybersecurity RFP Responses?
Responding to cybersecurity RFPs manually is slow for reasons that go beyond volume. The same security controls are explained repeatedly across technical sections, questionnaires, and compliance matrices.
Inputs come from sales, security, legal, and compliance at different times, often using different source documents. The result is inconsistency, rework, and review cycles that delay decisions.
AI changes this process by shifting effort away from rewriting and reconciliation toward review and validation.
Instead of starting from scratch or copying from older responses, teams generate drafts grounded in existing security knowledge, then focus on accuracy, scope, and alignment across the document.
1. AI Accelerates First Drafts Without Sacrificing Accuracy
AI-assisted drafting shifts the starting point. Instead of pulling a single past answer, AI generates a draft by referencing multiple relevant knowledge sources at once.
What changes in the workflow:
- First drafts are created using existing security documentation, not blank pages.
- Responses reflect current language patterns across multiple sources.
- Teams spend time reviewing and refining instead of assembling content.
2. Using Centralized Knowledge Sources for Security Content
Cybersecurity responses depend on many inputs: policies, prior RFPs, audits, architecture docs, and internal guidance. When these live in different systems, inconsistencies multiply.
With centralized knowledge:
- AI pulls from a single, governed set of security sources.
- The same definition of a control is used across the response.
- Updates to source material propagate into future drafts.
This reduces the risk of mixing old and new versions of the same answer.
3. Fighting Stale or Conflicting Security Answers
One of the hardest problems in cybersecurity RFPs is detecting when answers no longer align. Humans rarely notice drift until reviewers flag it.
AI helps by:
- Identifying conflicting statements across answers.
- Flagging content that has not been updated recently.
- Highlighting sections that contradict the defined scope or controls.
4. Improving Collaboration Across Sales, Security, and Compliance Teams
Cybersecurity RFPs require input from multiple teams, but coordination is usually manual.
AI-enabled workflows improve collaboration by:
- Giving all contributors access to the same source-backed drafts.
- Reducing repetitive questions to security and compliance SMEs.
- Allowing teams to review and comment in parallel instead of sequentially.
As cybersecurity RFPs grow longer and more demanding, manual response processes struggle to keep pace. Teams are expected to deliver accurate, consistent answers across technical, compliance, and legal sections under tighter timelines. That pressure helps explain why 73% of businesses have increased funding for AI, particularly in areas where speed and consistency directly affect outcomes.
Also read: Top 25 RFP Software in 2025: Which to Use?
How Inventive AI Transforms Cybersecurity RFP Responses?
Responding to cybersecurity RFPs requires speed without sacrificing accuracy, consistency across technical and compliance sections, and answers that can survive legal and security review.
Inventive AI is built specifically to address where cybersecurity RFP responses break down.
Here’s how Inventive AI supports cybersecurity RFP teams:
- 2× higher response quality that improves win rates: Produces clearer, more complete cybersecurity answers aligned to how security, legal, and compliance teams evaluate risk, contributing to up to 50% higher win rates.
- Context-aware answers grounded in the full RFP: Uses a multi-layer Context Engine to reason across the entire cybersecurity RFP, ensuring answers stay consistent across technical requirements, questionnaires, SLAs, and compliance sections.
- Automatic conflict detection across security responses: Flags contradictory statements in areas like incident response timelines, control ownership, and compliance claims before they reach final review.
- Outdated and non-compliant content detection: Identifies stale security answers by comparing responses against current approved policies, audits, and knowledge sources, reducing reuse of legacy content.
- Quality benchmarking against gold-standard security content: Evaluates every response for accuracy, completeness, and clarity, delivering 95% accuracy with 66% of answers requiring near-zero editing.
- Narrative-style cybersecurity proposal generation: Supports long-form content such as security overviews, incident response summaries, compliance explanations, and executive briefs, not just Q&A.
- Centralized security knowledge hub with live integrations: Pulls approved security content from systems like Google Drive and SharePoint to maintain a single source of truth and prevent content drift.
Inventive AI’s AI RFP Agent is purpose-built for high-risk, security-heavy RFPs where accuracy, consistency, and speed directly affect deal outcomes. It generates response drafts grounded in your approved security knowledge while continuously checking for conflicts, stale content, and scope mismatches across the entire proposal.
Frequently Asked Questions (FAQs)
1. What makes cybersecurity RFPs different from other RFPs?
Cybersecurity RFPs are reviewed by security, legal, compliance, and procurement teams at the same time. Responses are often treated as enforceable commitments and may be referenced later during audits, renewals, or incidents, which raises the bar for accuracy and consistency.
2. Why do cybersecurity RFP responses take so long to complete?
The same security controls are repeated across technical sections, questionnaires, compliance matrices, and contracts. Inputs come from multiple teams, and manual reconciliation of overlapping answers creates delays and rework.
3. How do buyers evaluate cybersecurity RFP responses?
Buyers look for clear explanations of how security controls operate, proof that those controls are enforced today, and consistency across the entire response. Inconsistencies or vague answers often trigger follow-up reviews or disqualification.
4. Can AI really be trusted for cybersecurity RFP responses?
AI is most effective when it drafts responses using approved internal security knowledge and flags conflicts or outdated content. Final validation still comes from security and compliance teams, but AI reduces manual drafting and review time significantly.
5. Who benefits most from AI-powered cybersecurity RFP software?
CROs, VPs of Sales, proposal managers, and security teams benefit the most. AI-powered RFP software helps them respond faster, reduce risk from inconsistent answers, and scale high-quality responses without adding headcount.

90% Faster RFPs. 50% More Wins. Watch a 2-Minute Demo.
Knowing that complex B2B software often gets lost in jargon, Hardi focuses on translating the technical power of Inventive AI into clear, human stories. As a Sr. Content Writer, she turns intricate RFP workflows into practical guides, believing that the best content educates first and earns trust by helping real buyers solve real problems.
After witnessing the gap between generic AI models and the high precision required for business proposals, Gaurav co-founded Inventive AI to bring true intelligence to the RFP process. An IIT Roorkee graduate with deep expertise in building Large Language Models (LLMs), he focuses on ensuring product teams spend less time on repetitive technical questionnaires and more time on innovation.


