What is the SIG Questionnaire? A Comprehensive Guide
Understand the SIG Questionnaire with this guide. Discover its purpose, users, core vs. lite types, and risk domain coverage. Buy now!

Introduction
For sales, proposal, and security teams, the deal doesn’t stall at pricing. It stalls at the SIG questionnaire. Before your buyer even considers signing, they need assurance that your company can protect their data.
According to a report from HubSpot and Ponemon, 42% of organizations state that their board of directors now expects formal proof that third-party risks are being properly evaluated. This growing demand for oversight at the board level indicates that formalizing vendor risk assessments is becoming a strategic priority for many companies.
The problem? SIG questionnaires are long, complex, and time-consuming. They span hundreds of questions across cybersecurity, compliance, data governance, and risk management, requiring input from IT, legal, and operations. For revenue teams, each unanswered SIG is a bottleneck that delays deal closures and stretches internal bandwidth.
This guide breaks down everything you need to know about the SIG questionnaire, from what’s inside, to who owns it, and most importantly, how to respond to it faster without compromising accuracy.
TL;DR
- A SIG questionnaire (Standardized Information Gathering) is a widely used security assessment tool sent to vendors to evaluate their data protection, compliance, and risk practices.
- There are three main types: SIG Lite (short, initial screening), SIG Core (comprehensive for high-risk vendors), and Customized SIGs tailored to specific buyer needs.
- Completing SIGs requires cross-functional input from security, legal, compliance, and proposal teams, and often takes 15–30+ hours manually.
- Common mistakes include outdated content, missing documentation, and inconsistent tone, slowing down deal cycles and reducing trust.
- Best practices include using a centralized response library, assigning domain-specific owners, maintaining content freshness, and automating reviews.
What is a SIG Questionnaire?
A SIG questionnaire, short for Standardized Information Gathering questionnaire, is a structured assessment tool designed to evaluate a vendor’s information security, privacy, and risk management practices.
Developed and maintained by the Shared Assessments Group, the SIG is widely adopted by organizations across industries such as finance, healthcare, SaaS, and government contracting to conduct third-party vendor risk assessments.
In essence, it serves as a due diligence framework that buyers send to vendors to ensure that their internal controls and security policies meet regulatory and operational expectations.
For vendors, completing a SIG is often a prerequisite to moving forward in the procurement process, especially when handling sensitive data, integrating with client systems, or delivering cloud-based services.
Since not all vendor relationships carry the same level of risk, the SIG framework is available in different versions. Let’s explore the main types of SIG questionnaires and when each is used.
Types of SIG Questionnaires

The SIG questionnaire isn't a one-size-fits-all document. To meet the varying needs of organizations based on risk level, business size, and regulatory exposure, the Shared Assessments Group offers the SIG in multiple formats, primarily SIG Core, SIG Lite, and SIG Customized.
Understanding the differences between these versions is critical for proposal and security teams so they can allocate the right resources and respond accurately without wasting time on unnecessary details.
1. SIG Lite
Purpose: Initial vendor screening or low-risk vendor engagement
Length: ~150–200 questions
Use Case:
- Used during early stages of vendor evaluation.
- Appropriate for vendors handling non-sensitive data or offering peripheral services.
- Often part of prequalification in an RFP or procurement process.
Focus Areas:
- General corporate information.
- Basic data protection and access control policies.
- Preliminary compliance and governance metrics.
Why it matters:
SIG Lite helps buyers quickly identify whether a vendor has the baseline security hygiene to continue into more detailed due diligence.
2. SIG Core
Purpose: Deep-dive security and risk evaluation
Length: 1000+ questions
Use Case:
- Required for critical vendors with access to sensitive data, infrastructure, or regulated systems.
- Often sent by enterprise IT, finance, or healthcare buyers who must meet regulatory obligations (HIPAA, GLBA, GDPR, SOC 2).
Focus Areas:
- Advanced controls for data encryption, identity access management, threat detection, incident response.
- Third-party oversight, subcontractor controls, and breach notification policies.
- Physical security, cloud architecture security, business continuity, and legal frameworks.
Why it matters:
A fast, consistent, and accurate response can accelerate deal closure, while delays or inconsistencies can stall or disqualify your proposal.
3. Customized SIG (Build-Your-Own)
Purpose: Tailored assessments based on buyer-specific priorities
Length: Varies
Use Case:
- Enterprises may modify or combine sections from SIG Core and SIG Lite.
- Used to address industry-specific risk areas (e.g., FedRAMP, PCI-DSS, HITRUST).
- Often used by global firms with complex compliance frameworks.
Focus Areas:
- Selectively chosen from Shared Assessment’s control domains.
- Buyers may request evidence, documentation, or policy attachments alongside responses.
Why it matters:
Customized SIGs demand even more coordination across proposal, IT, and compliance teams, and require structured content reuse to avoid duplication and errors.
Now that you know the formats, it’s important to understand why companies rely on SIG questionnaires in the first place, and what they’re trying to uncover.
Why Do Companies Use SIG Questionnaires?
As digital ecosystems grow more complex, organizations can’t afford to overlook the risks that come from third-party vendors. 62% of data breaches originate from third-party vendors. From data breaches and regulatory fines to reputational damage, the stakes are high. That’s why an increasing number of companies rely on SIG questionnaires as a standardized way to evaluate the security posture and risk exposure of their vendors, before doing business with them.
The Standardized Information Gathering (SIG) questionnaire enables procurement, IT, and risk management teams to make informed, consistent, and scalable decisions during the vendor selection and onboarding process.
1. To Evaluate Third-Party Risk in a Standardized Format
Traditional vendor risk assessments vary widely in format and quality. The SIG questionnaire creates a uniform benchmark across vendors, making it easier for buyers to assess and compare responses objectively.
2. To Ensure Regulatory and Security Compliance
Companies operating under frameworks like SOC 2, ISO 27001, HIPAA, GDPR, or PCI-DSS need to ensure their vendors are compliant too. The SIG provides a structured way to document vendor alignment with these regulations, minimizing audit risks and legal exposure.
3. To Accelerate the Procurement Process
With a comprehensive SIG, buyers can reduce the number of follow-up questions and redline cycles. A completed SIG allows teams to identify red flags early and avoid wasting time on vendors who fail to meet basic security criteria. According to Gartner, 60% of organizations say delays in vendor security assessments are a key blocker in contract execution.
4. To Increase Transparency and Trust
By requiring a vendor to complete a SIG, buyers gain insight into how the vendor operates behind the scenes i.e, how data is stored, who has access, how incidents are managed, and what contingency plans are in place. This fosters trust and strengthens long-term relationships.
5. To Reduce Legal and Financial Exposure
If a vendor experiences a breach or non-compliance issue, the buyer may also be held accountable. A completed SIG acts as evidence of due diligence and can reduce liability by proving the company took steps to evaluate vendor security before entering a contract.
SIG questionnaires help companies protect themselves financially, operationally, and reputationally. But for vendors, the challenge is clear: responding to these documents manually is inefficient, error-prone, and time-consuming.
With such high stakes involved, SIG responses require careful collaboration. So who’s actually responsible for completing these assessments?
Who Typically Responds to a SIG Questionnaire?
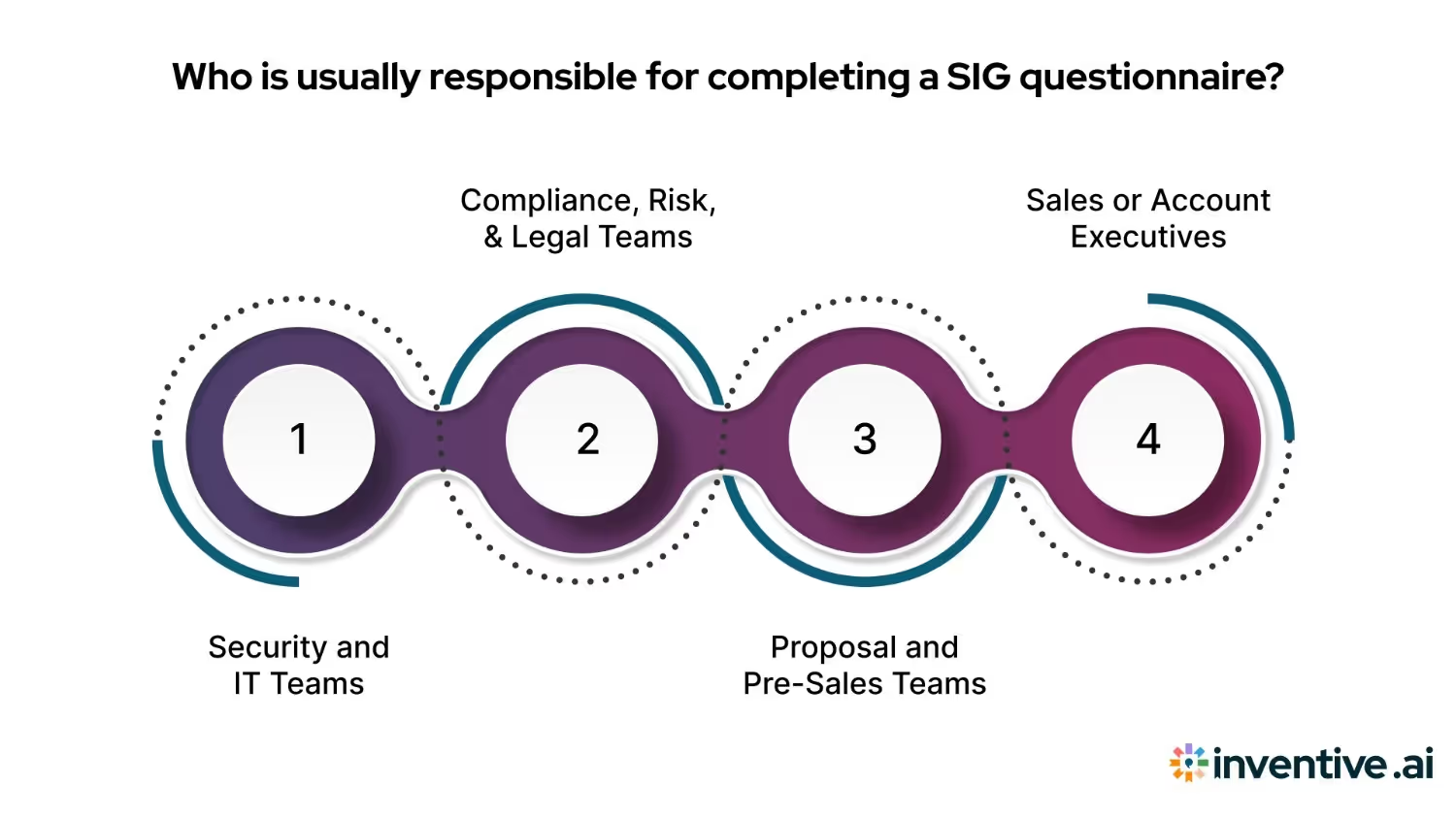
Each SIG includes hundreds of detailed questions spanning security controls, data privacy, compliance, and operations. That means multiple internal stakeholders must contribute accurate, up-to-date information to avoid delays, inconsistencies, or deal friction.
1. Security and IT Teams
These are the primary owners of technical questions related to:
- Network architecture and endpoint protection.
- Access control and identity management.
- Vulnerability scans, penetration tests, and incident response.
- Cloud infrastructure, encryption policies, and disaster recovery.
2. Compliance, Risk, and Legal Teams
These teams provide input on governance, regulatory alignment, and third-party oversight.
Typical contributions include:
- Certifications (e.g., SOC 2, ISO 27001, HIPAA policies).
- Data retention and privacy policies (e.g., GDPR).
- Breach notification protocols.
- Legal disclosures and risk management documentation.
3. Proposal and Pre-Sales Teams
Often the coordinators of the SIG response process, these teams:
- Manage timelines and ensure submission deadlines are met.
- Act as the bridge between technical SMEs and sales leaders.
- Review content for tone, consistency, and alignment with buyer expectations.
- Format the final deliverable and upload responses into the client’s procurement portal.
4. Sales or Account Executives
While not technical contributors, sales leaders are often the drivers of urgency. They:
- Track progress and push internal stakeholders to meet deadlines.
- Provide context on the buyer’s priorities and sensitivities.
- Ensure that responses align with the overall narrative of trust and partnership.
Knowing who responds is just one part of the equation. Next, let’s look at what these questionnaires actually include and why each section matters.
What Does a SIG Questionnaire Contain?
A SIG questionnaire (Standardized Information Gathering) is a structured assessment tool used by enterprises to evaluate a vendor’s ability to handle data securely, manage risks, and comply with regulatory standards. These questionnaires are comprehensive and domain-based, often consisting of hundreds of questions across key risk categories.
Each domain targets a specific area of concern, from access control to business continuity, and collectively, they help buyers determine whether a vendor meets the security and compliance standards necessary to move forward with procurement.
Access Control and Identity Management
This section focuses on how your organization manages access to systems, applications, and data. Buyers expect clarity on whether your company uses multi-factor authentication (MFA), how access is granted based on roles, and the process for deactivating accounts when employees leave. Identity management policies are scrutinized to ensure unauthorized users cannot access sensitive systems or client information.
Data Security and Privacy
One of the most heavily weighted areas in a SIG questionnaire, this section assesses how your company protects data throughout its lifecycle. Buyers want to know whether data is encrypted at rest and in transit, how you classify sensitive information, and what policies govern data retention and disposal.
In regulated industries, the questionnaire may also ask how your organization complies with data privacy laws such as GDPR, HIPAA, or CCPA. Demonstrating a mature data protection framework helps build trust and shortens procurement review cycles.
Network and Infrastructure Security
This domain explores the technical controls you have in place to secure your IT environment. Questions may cover the use of firewalls, intrusion detection and prevention systems, endpoint protection, and cloud security configurations.
Buyers want to ensure your network is segmented appropriately, patched regularly, and monitored for anomalies. A lack of infrastructure security can expose clients to downstream threats, making this a non-negotiable category in high-risk vendor evaluations.
Incident Response and Business Continuity
Vendors are expected to be prepared for worst-case scenarios, and this section is where buyers test that readiness. You’ll be asked to provide details on how you detect, report, and remediate security incidents, including who is involved and what response timelines are in place.
In parallel, the business continuity portion evaluates how your organization ensures uptime and resilience, including failover capabilities, disaster recovery plans, and results from regular tabletop exercises. Buyers look for proactive, documented procedures that minimize risk during crises.
Third-Party and Vendor Risk Management
Buyers are increasingly concerned not just with your security, but with the security of your vendors and subcontractors. This domain assesses how your organization manages third-party risk, whether you conduct annual assessments, require sub-vendors to meet equivalent security standards, and document third-party relationships.
Strong oversight of your vendor ecosystem reduces cascading risks and reassures buyers that your extended network doesn’t introduce vulnerabilities.
Security Awareness and Training
Human error remains one of the leading causes of data breaches, so this section evaluates how your organization trains and educates employees. Buyers will ask how frequently your teams undergo security training, whether you simulate phishing attacks, and how you document compliance with training requirements.
Organizations that demonstrate a culture of security awareness signal operational maturity and reduce the likelihood of insider-related incidents.
Governance, Risk, and Compliance (GRC)
This section focuses on your overall governance structure and how you manage organizational risk. Buyers expect to see documented policies, an internal audit process, and defined ownership of security and compliance responsibilities.
If your organization is certified in standards like ISO 27001 or SOC 2, this is where you provide proof. Effective governance frameworks show that your security program is not just reactive but strategically managed.
Physical Security and Facility Controls
Although digital threats dominate headlines, physical risks are still very real, especially for vendors that host infrastructure on-premises or use hybrid environments.
This section addresses building access controls, surveillance systems, environmental safeguards, and visitor management policies. Buyers want assurance that physical access to sensitive systems is tightly controlled and monitored at all times.
Supporting Evidence and Documentation
Beyond answering questions, buyers often request documentation to validate your responses. This might include incident response plans, data flow diagrams, audit logs, training records, or certification reports. Your ability to provide complete and current documentation can speed up security reviews and prevent additional follow-ups.
A SIG questionnaire covers far more than surface-level security. It’s a deep-dive into your company’s operational readiness, risk posture, and overall trustworthiness. However, responding to these questionnaires manually is time-consuming and difficult to scale.
With a clearer picture of what buyers expect, it’s time to focus on how to manage your responses effectively and avoid the delays that cost deals.
Best Practices for Effectively Responding to a SIG Questionnaire
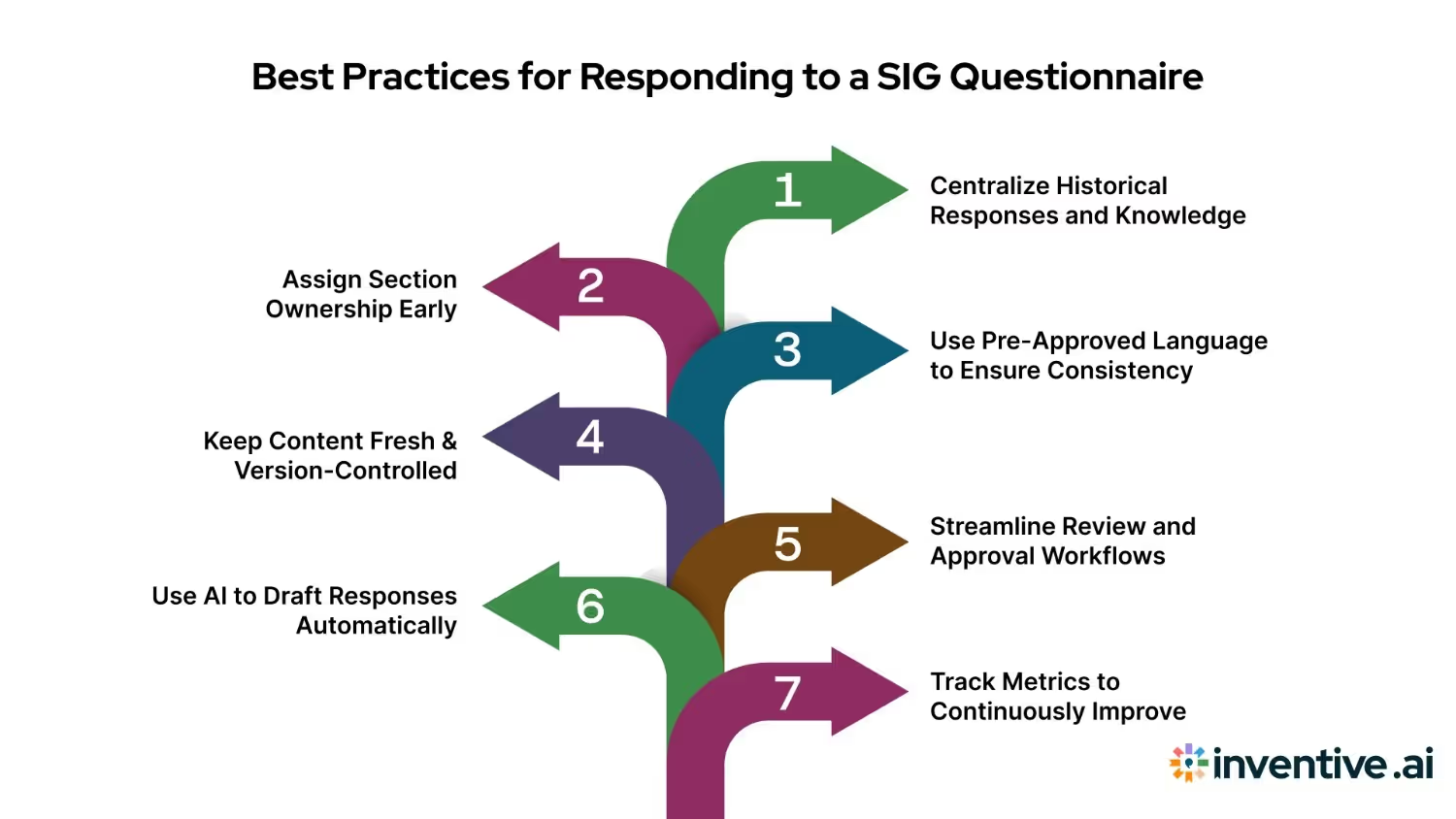
Responding to a SIG questionnaire is a high-stakes process. It often determines whether your company moves forward in a deal, passes due diligence, or is eliminated from consideration. Yet for many sales and proposal teams, the process remains manual, repetitive, and fragmented, spread across disconnected documents, legacy templates, and siloed teams. To stand out and avoid bottlenecks, your SIG response needs to be complete, accurate, and fast.
Here's how to do it effectively.
1. Centralize Historical Responses and Knowledge
The first step toward a faster, more consistent SIG response is building a centralized knowledge base. Many of the questions in SIG questionnaires overlap across deals and clients, which means reusable content is your most valuable asset. Storing validated answers, along with supporting documentation like certifications, process maps, and security policies, in one shared hub allows teams to pull accurate responses without starting from scratch every time.
2. Assign Section Ownership Early
SIGs often span domains like IT, compliance, legal, and operations. Waiting until the last minute to track down inputs leads to missed deadlines and inconsistent responses. A best practice is to assign clear ownership of each domain to relevant subject matter experts (SMEs) at the outset. Proposal managers or RFP coordinators should act as the central point of control, ensuring inputs are submitted on time, reviewed for accuracy, and approved by all relevant stakeholders.
3. Use Pre-Approved Language to Ensure Consistency
When multiple people contribute to the same questionnaire, inconsistencies in tone, technical depth, and messaging often emerge. This can confuse reviewers or create a perception of risk. To avoid this, teams should standardize answers using pre-approved, reviewed content, ensuring that technical explanations align with how your organization wants to be perceived.
4. Keep Content Fresh and Version-Controlled
One of the biggest risks in SIG responses is using outdated or conflicting information. A previous year’s response or a retired policy can be a red flag during security evaluations. It’s critical to maintain a system that flags stale content and allows easy version control across all questionnaire submissions.
5. Streamline Review and Approval Workflows
Responses to SIG questionnaires often require multiple rounds of internal review, especially when they touch on regulatory or legal commitments. Instead of emailing Word documents or tracking edits manually, use a collaborative platform that supports real-time editing, commenting, and audit trails.
6. Use AI to Draft Responses Automatically
Perhaps the biggest shift in responding to SIGs effectively is the introduction of AI-assisted drafting. Instead of manually assembling content from various teams, Inventive AI analyzes the questionnaire, maps questions to previous answers, and generates first drafts within minutes. These drafts are highly contextual, drawing from your organization’s past responses, documents, and knowledge systems. Teams can then focus on refining instead of writing from scratch, accelerating throughput without compromising quality.
7. Track Metrics to Continuously Improve
Just as sales and marketing teams measure campaign effectiveness, proposal and security teams should track SIG response KPIs. Monitor how long it takes to complete responses, how many contributors are involved, and where delays typically occur. This data helps identify process bottlenecks and optimize workflows over time.
Even well-intentioned teams can stumble. Let’s look at the common pitfalls that slow SIG responses down, and how you can avoid them.
Common Mistakes to Avoid When Completing SIG Questionnaires
Completing a SIG questionnaire is about proving your organization is trustworthy, compliant, and enterprise-ready. However, even experienced teams fall into traps that can delay approvals, raise red flags, or derail deals entirely.
Below are some of the most common mistakes vendors make during the SIG response process, and how to avoid them.
1. Reusing Outdated or Inaccurate Content
One of the most frequent missteps is copying and pasting responses from previous questionnaires without verifying their accuracy. Security policies evolve, infrastructure changes, and certifications expire, but many teams fail to keep their response libraries updated. Using outdated answers not only weakens your credibility but can lead to unnecessary follow-up questions or outright disqualification.
2. Responding Without Input From Subject Matter Experts
Attempting to complete a SIG questionnaire without looping in domain experts, such as security leads, compliance officers, or IT managers, can lead to vague, technically incorrect, or incomplete answers. Many questions require detailed operational insight that only SMEs possess. Overlooking this step may result in answers that sound generic or fail to meet buyer expectations.
3. Inconsistent Tone and Terminology Across Sections
When multiple contributors are involved, inconsistencies in tone, technical language, or terminology can creep in. One section may be written in legal jargon while another sounds overly casual or vague. This inconsistency undermines the professionalism of your submission and may confuse reviewers.
4. Ignoring Evidence or Documentation Requests
Many SIG questionnaires include requests for supporting evidence, such as SOC 2 reports, data flow diagrams, or incident response policies. Failing to attach the correct documentation or ignoring these fields entirely signals poor preparedness.
Always have a documentation checklist mapped to SIG sections and ensure the latest versions are accessible in your knowledge base.
5. Rushing the Final Review Process
Even well-prepared responses can go awry if the final review is rushed or skipped altogether. Teams under pressure may skip proofreading, fail to spot inconsistencies, or submit incomplete sections. This introduces risk at the last mile of the process. A structured approval workflow is critical, ideally one that includes validation from SMEs, legal, and proposal owners.
6. Underestimating the Strategic Importance of SIGs
Some vendors treat SIGs as an afterthought, responding reactively and prioritizing them only when pushed by the buyer. But in many deals, especially in finance, healthcare, and SaaS, a poorly executed SIG can halt a contract, even if the proposal is technically sound. Treating the SIG process as a strategic sales asset rather than a compliance formality positions your team as trustworthy and enterprise-ready.
To take your process from reactive to strategic, these best practices can help your team respond to every SIG with clarity, consistency, and speed.
Best Practices for Managing SIG Questionnaire Responses

Completing a SIG questionnaire is about building trust with your buyer through clarity, speed, and consistency. To move deals forward without friction, high-performing teams don’t treat SIGs as ad hoc tasks; they develop a sustainable system that can support multiple stakeholders and scale with demand.
Here’s how to do it right.
1. Establish a Structured Knowledge Foundation
Instead of starting from scratch each time, create a centralized content hub where previously approved answers, policy documents, certifications, and technical diagrams are stored and indexed. This foundational step allows teams to pull verified information efficiently, reduce duplication, and maintain accuracy.
2. Define Ownership and Roles Early
SIGs touch on multiple domains, from encryption practices to HR policies, which means no single team can handle it alone. Assign subject matter experts (SMEs) to specific categories and ensure they’re looped in from the beginning. This eliminates last-minute fire drills and promotes accountability.
3. Maintain Consistency Across All Responses
Buyers review dozens of vendor submissions, consistency in tone, terminology, and formatting is a subtle but powerful trust signal. Whether it’s the way you reference frameworks like SOC 2 or how you describe access controls, alignment matters.
4. Integrate Documents Seamlessly Into the Workflow
SIG responses often require supporting documentation like audit logs, penetration test results, or policy excerpts. Hunting for these assets in fragmented folders wastes time and increases the risk of attaching outdated versions.
5. Build a Repeatable Review and Submission Process
Even if your content is strong, a disorganized review cycle can cause unnecessary delays. Create a defined workflow for reviews and approvals that involves all relevant stakeholders, technical leads, compliance officers, and legal advisors.
6. Refresh Content on a Defined Schedule
Security postures evolve, certifications renew, and regulatory standards change. That’s why a living content strategy is critical. Set a routine i.e., monthly, quarterly, or biannually, to audit your SIG library.
7. Operationalize SIG Response as a Competitive Advantage
Instead of reacting to every new SIG as a time-sensitive chore, develop a response strategy that aligns with your revenue goals. The vendors who win aren't just compliant, are fast, clear, and easy to work with. By embedding automation, collaboration, and strategic foresight into your SIG workflow, you position your company as a mature, security-forward partner.
While best practices help, manual processes still leave room for error and delay. That’s where automation makes a measurable difference.
How AI Is Shaping SIG Questionnaires?
As third-party risk assessments become more complex and time-sensitive, organizations are turning to artificial intelligence to streamline the way they respond to SIG questionnaires. Rather than relying on spreadsheets, versioned Word docs, or basic knowledge, AI introduces speed, structure, and scalability into the process.
Here’s how AI is reshaping SIG response workflows across industries:
1. AI-Driven Content Retrieval
AI systems can parse large content libraries to retrieve previously approved answers that match new SIG questions. Using natural language processing (NLP), these tools understand question intent, even when phrased differently, and map them to stored responses, reducing duplicate effort and increasing consistency.
2. Automated Drafting and Question Matching
Some platforms now offer AI-generated draft answers based on prior submissions, documentation, and compliance records. These systems identify key terms in each question (e.g., "data encryption" or "MFA") and auto-fill relevant, context-aware content. This dramatically reduces manual writing and increases accuracy.
3. Semantic Categorization and Template Recognition
SIG questionnaires vary in format and length, but AI can categorize questions by domain (e.g., governance, privacy, cloud infrastructure) and align them to internal SMEs or prebuilt templates. This allows teams to break down massive SIGs into manageable, role-based tasks.
4. Language Normalization and Tone Alignment
AI tools now assist in rewording responses for clarity, tone, and compliance, ensuring that technical content is both accessible to non-technical reviewers and consistent across all sections. This helps organizations present themselves as mature and audit-ready vendors.
5. AI-Powered Review Assistance
AI is increasingly used to flag responses that may be outdated, incomplete, or contradictory. Some systems assign a “confidence score” or suggest supporting documents for verification. This assists compliance teams in prioritizing final review efforts.
6. Knowledge Graphs and Contextual Linking
Advanced AI solutions build internal knowledge graphs that connect documentation, past responses, certifications, and SME inputs. These graphs enable smarter decision support such as suggesting when to reference a SOC 2 report or link to a DRP policy, within the flow of work.
7. Continuous Learning from Past Responses
Many AI systems now learn over time by analyzing response patterns, approval history, and feedback loops. This helps improve answer quality and reduces repetitive work in future questionnaires.
AI in SIG response management is about reducing friction. By automating repetitive tasks, recommending relevant answers, and enforcing structure, AI allows teams to focus on strategic review and cross-functional alignment. As buyer expectations grow and cybersecurity scrutiny increases, utilizing AI is becoming essential.
How Inventive AI Simplifies the SIG Questionnaire Process?
If your team spends days juggling SIG questionnaires, digging through outdated documents, coordinating across security, compliance, and sales, and double-checking answers for consistency, you’re not alone. For vendors in SaaS, healthcare, fintech, or infrastructure, SIG responses have become a slow, high-stakes bottleneck that threatens deal velocity.
Buyers expect fast, complete, and accurate security responses. But when documentation lives in scattered spreadsheets, past questionnaires, and inboxes, delays are inevitable. The outcome? Missed deadlines, compliance risks, and stalled contracts.
What if you could cut SIG response time by 90%, without hiring additional staff or risking security errors?
Inventive AI’s AI-Powered RFP Response Software is built to handle the complexity of security questionnaires like SIG Lite and SIG Core. It automates drafting, centralizes knowledge, and streamlines reviews, so your team can focus on accuracy, not admin.
- 90% Faster SIG Response Completion
Responding to a SIG used to mean 20–30 hours of manual coordination between security, IT, legal, and sales. With Inventive AI, teams generate complete first-pass answers in under 3 hours, allowing more time for refinement, fewer missed deadlines, and faster progression through procurement.
- 10x Faster Drafts from a Verified Content Library
Inventive AI pulls approved, up-to-date content from your knowledge base, security policies, certifications (e.g., SOC 2, ISO 27001), and past SIGs. No more searching through folders or forwarding PDFs. Your team responds with confidence using validated information.
- 95% Accuracy Using Confidence-Scored Answers
All AI-generated responses are tied to your organization’s official documentation, evidence attachments, and policy repositories. Responses are scored by confidence level, helping reviewers focus only where human oversight is needed, minimizing rework and risk.
- 3x More Security Questionnaires Completed With the Same Team
Proposal, compliance, and security teams using Inventive AI report up to a 3x increase in throughput, without expanding headcount. With content reuse, auto-tagging, and approval workflows, your team completes more SIGs, faster, without late nights or last-minute stress.
- Real-Time Collaboration for Cross-Functional Inputs
Integrated with Slack and Microsoft Teams, Inventive AI keeps stakeholders aligned. Assign sections to IT, legal, or compliance teams; track approvals; and gather input, all within one unified workspace, eliminating email back-and-forth.
- Automated Detection of Content Gaps and Inconsistencies
Inventive AI highlights incomplete or outdated answers before submission, flagging discrepancies in SLA references, expired certifications, or mismatched compliance claims. This prevents rejections and builds buyer confidence in your security posture.

Here’s why it matters for security, compliance, and proposal teams -
- Cut time spent on SIG questionnaires by up to 90%.
- Eliminate manual copy-paste, version confusion, and outdated content risks.
- Collaborate across teams to generate complete, consistent answers faster.
- Maintain audit readiness with real-time document linking and version control.
- Respond to more questionnaires without overloading your core team.
Conclusion
For modern vendors, SIG questionnaires are a critical gatekeeper to enterprise deals. Whether you're closing a contract with a global financial institution, onboarding with a healthcare provider, or scaling into regulated markets, your ability to respond to SIGs quickly and accurately directly impacts your deal velocity and credibility.
But traditional SIG response workflows reliant on scattered documents, siloed teams, and manual coordination are too slow for today’s security-conscious buyers. As risk assessments become deeper and more frequent, automation is essential.
If your current SIG response process is holding back your sales cycle, it’s time for a smarter, faster way to deliver.
FAQs
What is a SIG questionnaire used for?
A SIG (Standardized Information Gathering) questionnaire is used by organizations to assess the security, privacy, and risk management practices of third-party vendors. It ensures vendors meet required compliance standards before contracts are signed.
What’s the difference between SIG Core and SIG Lite?
SIG Lite is a shorter, high-level version used for preliminary assessments or low-risk vendors. SIG Core is a comprehensive, detailed questionnaire with over 1,000 questions, typically required for vendors involved in sensitive or high-impact services.
How long does it take to complete a SIG questionnaire?
Manually completing a SIG questionnaire can take anywhere from 15 to 30 hours, depending on the version and internal coordination. With AI-powered tools like Inventive AI, this time can be reduced to under 3 hours.
How can Inventive AI help with SIG questionnaires?
Inventive AI automates response drafting using your approved documentation, tracks version history, flags outdated content, and enables real-time collaboration across teams. It helps you complete SIGs up to 90% faster while improving accuracy and consistency.

90% Faster RFPs. 50% More Wins. Watch a 2-Minute Demo.
Tired of watching deal cycles stall due to manual questionnaire back-and-forth, Dhiren co-founded Inventive AI to turn the RFP process from a bottleneck into a revenue accelerator. With a track record of scaling enterprise startups to successful acquisition, he combines strategic sales experience with AI innovation to help revenue teams close deals 10x faster.
Understanding that sales leaders struggle to cut through the hype of generic AI, Mukund focuses on connecting enterprises with the specialized RFP automation they actually need at Inventive AI. An IIT Jodhpur graduate with 3+ years in growth marketing, he uses data-driven strategies to help teams discover the solution to their proposal headaches and scale their revenue operations.


.jpeg)